Intro
One of the great features of FIM is that it is relatively easy to plugin custom functionality. You can extend the synchronization engine by developing rules extension and you can add custom workflows to the FIM portal. Rules extensions run under the FIM synchronization service account, workflows under the FIM service service account. This article describes an approach to enable communication to external systems (eg Exchange). Because you typically do not grant a service account rights to Microsoft Exchange, you need the ability to run part of your code using different credentials.
Encrypt password
You do not want to have passwords in clear text in configuration files or source code. That is where encryption comes into play. Encryption can be handled in a myriad of different ways. The method described here uses powershell cmdlets, which keeps it quite simple and understandable.
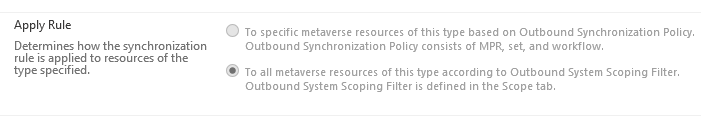 Instead of searching for the workflow that adds the sync rule, the MPR that triggers the workflow and then going to the set definition of the target population of the MPR, you can just examine the outbound scoping filter of the sync rule itself.
Instead of searching for the workflow that adds the sync rule, the MPR that triggers the workflow and then going to the set definition of the target population of the MPR, you can just examine the outbound scoping filter of the sync rule itself.